The Connection, Inc Blog
It’s easy to skimp here and there when you run a business. After all, it isn’t cheap, and you have to make difficult decisions every day for where you’re prioritizing your spending. One area where you can’t scrimp on a substandard investment is your technology; especially an old computer that has broken down over and over again. If you’re not careful, that broken computer could be holding you back and costing you profit.
How much time do you waste every day while trying to find specific files? Chances are, it’s more than you’d like, and one quick glance at your digital workspace would tell us you have some tidying up to do. Today, we want to share three tips to help you be more organized and productive with your digital workspace.
The sun is setting on an era. On October 14, 2025, Windows 10 will officially reach its end of support. For millions of users worldwide, this marks a significant turning point, prompting questions, concerns, and perhaps a touch of nostalgia for an operating system that has served faithfully for a decade.
So, what exactly does end of support mean, and what should you be doing now to prepare? Let's dive in.
Businesses are constantly seeking ways to build agility. Like many things, it’s not as easy as just saying it. If your current technology feels more like a roadblock than a launchpad, it might be time to explore some different strategies. Let's talk about MACH architecture, the powerful framework designed to build a flexible, scalable, and future-ready digital workplace.
Entertainment has changed a lot over the past several decades. When not too long ago teams of trained professionals were using ultra sensitive film stock to shoot your favorite movies, flatbed editors in dark rooms to edit them, and elaborate film projectors to show them, today there are digital cameras that rely on digital storage, digital editing that you can do from a phone, and OLED screens that use thousands of pixels to provide the clearest picture possible.
Support for the Microsoft Windows 10 operating system is coming to an end, so let's talk about something crucial for your business technology: upgrading as soon as possible. Microsoft has officially set the date: October 14, 2025. After this day, mainstream support for Windows 10 concludes. While that might seem like a comfortable distance away, in terms of IT planning and business operations, it's practically tomorrow. Waiting is not a strategy; planning is.
Artificial intelligence is taking over enterprise computing. So much so that there is some degree of cynicism among CIOs and other technology leaders about what exactly AI can do for them. The reality is that AI can do some pretty remarkable things and is advancing pretty quickly, but if you are expecting it to transform your business with minimal effort, you might be in for a rude awakening. This month, we want to take a look at how AI is beneficial for businesses and what to expect from the technology in the near future.
Have you ever searched for something on Google, played a game that remembers your high scores, or checked your Instagram messages? These apps feel smooth and efficient thanks to something called a Database Management System (DBMS) working quietly in the background. In this month’s newsletter, we’ll explore what a DBMS is, how it works, and why it’s essential for creating a seamless user experience.
Any computer issue you have can be extremely frustrating, but when something happens you should know you’re not alone. There are a few things that anyone that uses a computer has dealt with. This month, we take a look at three extremely common technical problems people deal with and what to do about them.
Operating systems are the backbone of any computer or device. Whether it’s your phone, a tablet, or a computer, the operating system controls how the device works, allowing you to run apps, browse the web, and complete tasks. For businesses, having up-to-date operating systems is especially important. Let's look at why this is critical and what can happen if businesses don’t keep up!
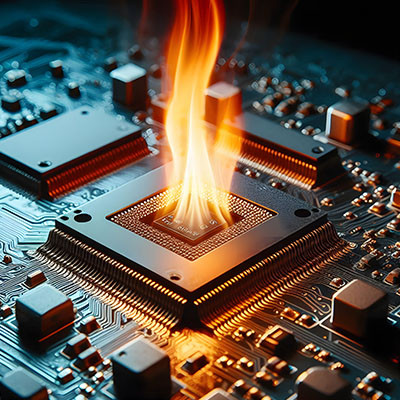
Your computer has a brain, of sorts, in its CPU… a tiny square that literally enables everything the device does, as it processes billions of instructions at a time. Of course, to support this on such a relatively tiny piece of hardware, most CPUs are packed with microscopic transistors—these transistors being small enough to fit hundreds on a single blood cell.
As you might imagine, this means things can go wrong pretty easily… and gone wrong, things have. Many newer computers are suffering from a bug that could cause permanent damage to the CPU… and if you don’t take steps fast, it could be too late.
With little fanfare, the AI Wars have begun. When we say “war” we mean just that: a battle for the survival of tools designed to improve human productivity. To start we should rewind a little. Most new software platforms (and many, many established ones) have started to use “artificial intelligence” to improve their products, or at least improve the prospect of selling them. In this week’s blog we will discuss the increased prevalence of “AI” and how some of the largest names in computing have gone all in on the technology.
How can you know when your organization should upgrade its technology infrastructure? The truth is that it’s not always immediately obvious when you should do so, as there are countless factors in play to consider at any given time. Today, we want to help your business determine when to bite the bullet and upgrade your technology.
The use of technology is one of the things that brings most people together. For the past couple of decades people have depended more and more on technology as a way to manage their lives, socialize, and get the goods and services they choose to purchase. This has led to the development of a lot of solid technology-related television shows. In this week’s blog, we thought we would take a look at three shows that cover multiple genres that are solid viewing for the technology enthusiast.
Software makes business run: that is an undeniable statement. From the operations software that allows your business to manage and pay its people to the CRM that provides a pathway to communicate efficiently with customers, to all of the applications that it takes to conduct business in earnest, software plays a crucial role in your business’ success.
It’s easy to open up far more tabs on your web browser than you need, especially when so many tools are cloud-based. If you find yourself in need of a quick way to close all other tabs besides a handful or so, we’ve got just the tip for you. You can close all open tabs to the right of your preferred window, or you can close all tabs outright.
Regularly, when a business is searching for ways to move their operations forward, there is a little hand wringing on how to do so. Every decision your business has to make comes with a price tag, and the more that you can do without spending a lot of money, the more value you are going to see. For this week’s blog, we thought we’d take a look at some actions you can take with your technology to ensure that your business is going in the right direction.
Computers allow businesses to do so much, but eventually a time comes to purchase new hardware. Thankfully, you can stave off this need pretty well by simply taking care of your existing technology. Here are some tips you can implement to make sure that your computer lasts as long as possible before it kicks the bucket.
News & Updates
Understanding IT
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Contact Us
Learn more about what The Connection can do for your business.
The Connection
51 Village CT
Hazlet, New Jersey 07730