The Connection, Inc Blog
Absolutely nobody likes dealing with passwords. They’re annoying, hard to remember, and yet, somehow, hackers seem to have no problem cracking them. That’s where password managers come in. They take the stress out of remembering a hundred different logins while keeping your business secure. If you’re still relying on sticky notes or using the same password for everything so you can remember it, it’s time to make the switch.
Running a business is basically a never-ending series of potential disasters just waiting to happen. Some are easy to fix, change a process here, tweak a strategy there—but others? They can completely derail your operations if you’re not prepared. That’s where smart technology steps in to save the day.
Let’s look at some nightmare scenarios that could spell disaster unless you have the right IT in place.
Think about how many online accounts you have. With so many accounts, it’s important to make sure they’re secure. Creating strong passwords is one of the best ways to protect your accounts from hackers. Here’s how you can create passwords that are hard to crack and keep all your online accounts safe.
Technology is central to most businesses, which means that security is, by proxy, central to them as well. With cyberattacks on the rise, it’s more important than ever for you and your employees to be on the same page regarding cybersecurity. Today, we are looking at four ways you can ensure sound cybersecurity practices that even the most belligerent employees can follow… with the right support in place.
Protecting your business’ accounts is something we will advocate for on repeat. You’ll hear us tell you about complex and unique passwords and multi-factor authentication until you’re sick of hearing it. But one tool that our clients sometimes forget is the password manager—an equally useful tool that can help your business keep passwords safe and secure.
Network security is a major issue for any business that relies on password-protected systems—and who doesn’t? With so much at stake, it’s important that every user uses passwords that are not only complex and secure but also easy to remember. This month, we will discuss how the passphrase is the answer to keeping your password-protected accounts secure.
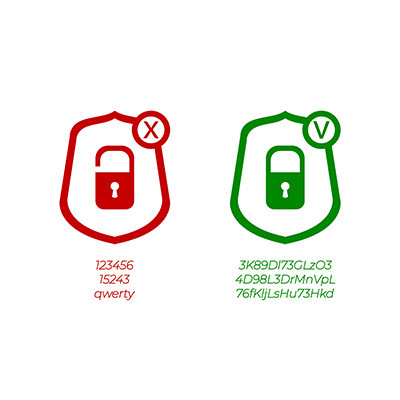
You should always use strong passwords for each and every account. Cybercriminals don’t need to put much effort into cracking a password these days—it only takes a little software and standard computer hardware to crack millions of passwords in just a second or two.
The more complex and random a password is, the more secure it is.
But coming up with (and memorizing) complex passwords is really difficult. This trick should make it a whole lot easier.
Safeguarding your online accounts is an important part of maintaining network security. With the increasing number of cyber threats, relying on strong, unique passwords is no longer optional—it's a necessity. Remembering complex passwords for numerous accounts can be challenging, however. This is where password managers come in handy, offering a secure and convenient solution to managing your credentials.
Passwords are one of the most important parts of keeping any account secure, and if you were to gain access to these accounts, you’d have access to personal data, subscriptions, money, and even the victim’s identity. Today, we want to show you just how easy it is to steal a password and gain access to an account.
Did you know that tomorrow is World Password Day, 2023? As the result of a campaign to spread awareness of the importance of sufficiently secure passwords, it has become an annual reminder of how critical sufficient passwords are to proper cybersecurity…despite passwords not being sufficient protection on their own. In light of tomorrow’s observance, let’s take some time to review why passwords are important to get right, and what else you need to have in place.
Multi-factor authentication is great when it works, but when it doesn’t, it can leave you in a pretty difficult situation. After all, what happens when all of a sudden, you cannot access your secondary authentication methods? We’re here to help you bypass this particularly challenging and frustrating scenario.
Simple passwords are just not an effective security practice, so if you’re still using credentials like Password, 123456, Guest, or Qwerty, listen up. You need better password hygiene practices before you suffer from a data breach. Here are some ways you can make a better password to protect your business from threats.
Nobody wants to spend their weekend doing paperwork. Nobody wants to spend several evenings in a row sitting over a laptop and slowly digging through every online account they have, resetting every password and carefully documenting everything in a secure password manager. I know this better than anyone, because I forced myself to do it.
Here’s the thing though, EVERYBODY should do it. As soon as possible.
Passwords are just one part of a comprehensive security strategy, but they are a crucial one. You must make sure that you are investing adequate time and effort into making sure your passwords are secure. This is easier said than done, but by the end of today’s short blog article, you’ll have all the information you need to craft excellent passwords for your accounts.
With many businesses’ increased reliance on their information systems and other IT, they need to do everything they can to keep those systems up and running and secure. This not only includes rolling out security systems that support that goal, it also demands they take the action necessary to keep these systems secure. Let’s look at four things you need to do to keep your business’ IT as secure as possible.
Businesses sure use a lot of online accounts, and if they don’t keep track of the passwords associated with these accounts, things can get messy fast. To help with this effort, password managers, or applications that store passwords in an encrypted vault, have really taken off. Here are some of the reasons why businesses invest in password management solutions.
Two-factor authentication is commonplace in the office environment, but it’s not commonplace enough, if you ask us. Too many organizations pass on it, placing their security at risk for no good reason. While the methods might vary, the benefits of two-factor authentication are too good to ignore. We’ll walk you through how to set up two-factor authentication for three of the most common accounts in the business environment: Microsoft, Google, and Apple.
News & Updates
Understanding IT
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Contact Us
Learn more about what The Connection can do for your business.
The Connection
51 Village CT
Hazlet, New Jersey 07730