The Connection, Inc Blog
Most organizations are trying to figure out how to secure their IT against the constant flood of threats out there. Unfortunately, the biggest threat out there isn’t something that you can actively protect against. Can you guess what it is?
Unfortunately, it’s your employees, and their potentially lax password practices—and while you can’t really protect yourself against insecure passwords, you can minimize the likelihood that they’ll be used.
Passwords are probably the most important part of keeping accounts secure. That’s why it is so important to follow industry best practices when creating them. Today, we’ll take a look at the standards outlined by the National Institute of Standards and Technology (NIST) in creating the best and most secure passwords.
You might know your Wi-Fi password, but can you tell your new staff members, guests, and clients, what it is off the top of your head? If you don’t write your password down, or store it somewhere that’s easily accessible, it can be difficult to remember; especially if it’s long and complex like it should be. Thankfully, if you already have a computer connected to the network, you can easily find out what your Wi-Fi password is.
Do you loan out your Netflix password to friends so that they can catch up on their favorite shows? If so, you’re in violation of a recent federal court ruling, which declares that sharing a password of any kind is now a federal offense. So, if you plan on watching the new Netflix original series Stranger Things, you may want to reconsider how you plan to do so.
Imagine a world where there wasn’t a singular dishonest being. Passwords would simply vanish from our everyday lives, as we would not be paranoid of a breach or other forms of cybercriminal activity. The harsh reality is this will never become reality. Even worse, the cybercriminals don’t just skim for lack of passwords. Instead, the dishonest criminal goes even further; they take advantage of common or recurring passwords. So how do you know if your password practices are leaving you vulnerable? Google is here to help.
All that stands between hackers and your accounts’ data, be it personal information or sensitive business info, is a measly string of characters that may (or may not) be complex enough to thwart their attacks. We’re talking about your passwords, and for many businesses, they are the only thing protecting important data. We’ll walk you through how to make sure your passwords are as complex as possible, as well as instruct you on how to implement additional security features to keep your data locked down.
Security is one of the most crucial pain points of all businesses, but sometimes it can be tricky to implement solutions if you’re not sure what you specifically need. Network security isn’t easy, but it doesn’t necessarily have to be hard. If you have difficulty reinforcing a security state of mind in your office, we have good news for you; by keeping these tips in mind, you’ll be able to keep your business more secure than it would be otherwise.
 It seems like we can’t go on the Internet without reading about some sort of data breach. Sometimes they’re caused by poor security measures, like lack of data encryption or two-factor authentication; other times, it’s because of lackluster password security. Despite the antiquity of the username and password, they’re staples in the modern office. Thus, it’s important that they’re as secure as possible at all times.
It seems like we can’t go on the Internet without reading about some sort of data breach. Sometimes they’re caused by poor security measures, like lack of data encryption or two-factor authentication; other times, it’s because of lackluster password security. Despite the antiquity of the username and password, they’re staples in the modern office. Thus, it’s important that they’re as secure as possible at all times.
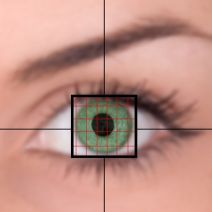 Humans are always trying to improve security protocols that can protect against increasingly advanced online threats. Unfortunately, the threats only grow stronger in response, and the war against malicious online activity rages on. Biometrics are security measures that are growing in popularity, but are expensive and difficult to integrate. Now, the US military is funding a campaign to make it more readily available to end users.
Humans are always trying to improve security protocols that can protect against increasingly advanced online threats. Unfortunately, the threats only grow stronger in response, and the war against malicious online activity rages on. Biometrics are security measures that are growing in popularity, but are expensive and difficult to integrate. Now, the US military is funding a campaign to make it more readily available to end users.
News & Updates
Understanding IT
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Contact Us
Learn more about what The Connection can do for your business.
The Connection
51 Village CT
Hazlet, New Jersey 07730









