The Connection, Inc Blog
Reliable IT advice is hard to come by, especially for cybersecurity. Whether it's uninformed coworkers or fake online influencers with their guides and platforms, most advice you find these days is bound to be outdated, incorrect, or both. You don’t want to base your business’ security around security myths, so we’re here to bust them today and offer you some guidance you can trust.
An expiration date helps to make sure you aren’t buying fast-turning foods at the grocery store, and now, the technology industry is making strides to establish a similar standard. A new industry report recommends new legislation pushing for End-of-Life (EoL) disclosure, which would, in theory, allow businesses and consumers alike to make more informed purchasing decisions. What does this mean for your business?
Running a small business is no easy feat, especially when it comes to managing supply chains. You’ve got to keep track of suppliers, shipments, inventory, and customer demands—all without losing your mind. Luckily, technology is here to help. Let's break down some of the key tech tools that small businesses are using to make their supply chains smoother and more efficient.
Your business’ data holds incredible potential for helping you improve operations, but only when it is leveraged properly. To this end, you have to identify specific metrics that you are working toward and establish how these metrics are helping you make strides forward. IT offers plenty of metrics to help you make better decisions about operational efficiency.
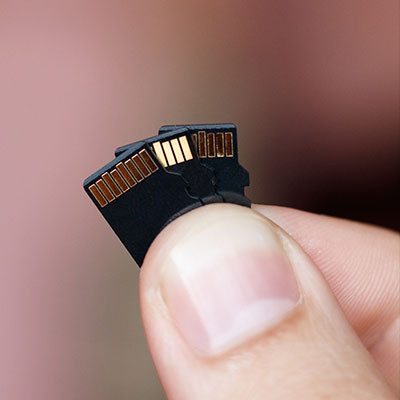
Do you ever think about how incredible technology is? In a world where it’s easy to take advantage of technology and devices that were practically inconceivable just a few short decades ago, it’s really amazing to just look at how far we’ve come, and how something so small can fit so much information.
Artificial intelligence has taken the world by storm, and the advent of emerging technologies has many small businesses thinking about how they can utilize it to cut costs, improve operations, and eliminate unnecessary or repetitive tasks. Let’s take a look at three ways your business can leverage artificial intelligence to the best of its ability.
The European Union’s General Data Protection Regulation (GDPR) has gone into effect, and with this new law comes a lot of information your organization needs to consider regarding individual data protection. In particular, the technology of blockchain is difficult to talk about in regard to GDPR, as it’s basically an encrypted and distributed digital ledger. How can blockchain work properly in tandem with the new GDPR regulations?
When you’re talking about something to do with a computer, you’re going to start hearing about some word that ends with “-ware.” You could probably list off a few yourself, but have you ever stopped to think about why they’re all described as “something-ware?” For this week’s Tech Term, we’ll take a peek at why we refer to things that way.
Why ‘Ware?’
It does seem like a strange part of the word, unless you look back to where we get it. According to Wiktionary, Software was first coined as a term in 1953, and was named based upon the fact that the term for the physical elements of the computer were already known as hardware. A quick peek into the online Merriam-Webster dictionary gives us a few definitions for the root of that word, ware.
The ones we’re concerned with are the first and the last definitions in the first entry: “manufactured articles, products of art or craft,” and “an intangible item (such as a service or ability) that is a marketable commodity.” We can combine these to give us a fair representation of what soft-’ware’ means: “manufactured articles to provide a service that is marketable.” After all, what is a computer program, if not an assortment of code meant to complete a specific task desired by a specific audience?
The word was first coined by Paul Niquette in 1953.
Different Software ‘Wares’
As you may imagine, there are plenty of varieties of ‘wares.’ Wiktionary.org offers a pretty impressive list of software types, with names derived from ‘-ware’, including the ones that you’ve already heard about, and some that are minutely specific. We’ll go over a few of these lesser-known varieties here:
Dreamware - This software type covers those that have not yet begun development and are still in the “what if there was a software that…” phase. Many of these projects never begin development, remaining something that some software developer once dreamt up.
Trialware - This variety of software is that which is only available to the user for a limited period of time, after which it is only available in a restricted form (if at all). This can be considered the free sample of software, offering just enough to make you want more.
Crapware - You know how a new computer often comes pre-installed with programs that you have no interest in, let alone the need for? This is what is known as crapware, as it takes up space without really offering anything to you. Another four-letter synonym for ‘crap’ can also be combined with “-ware” to make another, more forceful term for this variety.
Foistware - Malware can often come bundled with other, more legitimate software titles, to be installed without the user knowing. Of course, other programs can do this as well. Foistware is the term given to these software stowaways.
Fanware - Professionals aren’t the only ones capable of writing code, and even professionals will continue their coding in their off hours. Fanware describes the products that special-interest coders write to promote that interest.
Nagware - Another version of trialware, nagware describes a software title that will interrupt a user with persistent reminders to register it. Nagware will often disable the use of the program for short intervals during use, or display pop-up dialog boxes. In essence, this kind of trialware is designed to coerce a user into purchasing the full version through annoyance.
Garageware - This is a not-so-nice term for software that simply doesn’t perform as it should or has a lot of mistakes. The name is meant to suggest that the creators were total amateurs, developing this program literally in their garage.
Again, this is just a short list of the many different software varieties out there. What other ones have you heard of? Share them in the comments!
Businesses deal with compromises every day, whether it’s leaving late to let someone else get an early out or coming in on your day off to get a critical project finished on time. One of the compromises you absolutely don’t want to leave out is your business’ future. It’s up to you to acquire a solution that minimizes downtime without costing your organization an arm and a leg, but this is much easier said than done.
News & Updates
Understanding IT
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Contact Us
Learn more about what The Connection can do for your business.
The Connection
51 Village CT
Hazlet, New Jersey 07730